Autodesk Vault’s ADMS console is a powerful tool for managing and maintaining your vault server. While many administrators are familiar with using it to ensure backups are working and to monitor database size, there’s a feature that often goes unnoticed – the log files. In this blog post, we’ll shed light on the often overlooked Audit Logs within the ADMS console. These logs not only help in assessing the system’s health but also enable administrators to investigate user activities on the vault server. Let’s dive in!
Understanding Vault Audit Logs
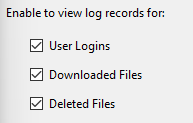
Audit logs, like other logs in the ADMS console, are text files that record specific events occurring on a vault server. They can be configured to track events such as user logins, file downloads, and file deletions. This feature allows administrators to monitor who is accessing the server, what files are being downloaded, and who is deleting files. Audit logs have proven invaluable in situations where files were unexpectedly deleted, providing a means to identify the responsible party.
Enabling Vault Audit Logs
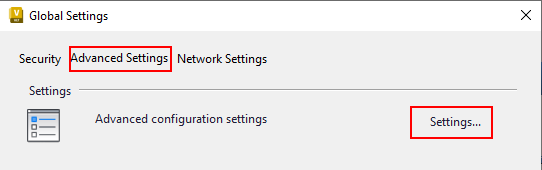
By default, the Audit logs are turned off in the ADMS console. To enable them, follow these steps:
Launch the ADMS console and navigate to Tools > Administration > Advanced Settings Tab > Advanced Configuration Settings.
While Autodesk Vault’s ADMS console is commonly used for backups and system maintenance, the power of its log files should not be overlooked. In particular, the Audit Logs offer valuable insights into user activities on the vault server. By enabling and leveraging these logs, administrators can gain visibility into who is accessing the server, what files are being downloaded, and who is deleting what files. This knowledge proves essential in maintaining data integrity, resolving issues, and ensuring a secure and efficient workflow within the Autodesk Vault ecosystem.
For more detailed troubleshooting guidance on utilizing Vault Log Files, refer to the Autodesk Help documentation here.
Unlock the potential of Audit logs in Autodesk Vault’s ADMS console and take your system monitoring and investigation capabilities to new heights.
For more information on this blog post, or if you have any other questions/requirements, please complete the below form: